Code in Search of a Home IV
And what to do with Big Blue and Apple too.
Preamble - Hat’s Off to IBM?
Big Blue bought Red Hat for 34 billion. Red Hat seems to be the only game in town. But Red Hat looks expensive today. The alternative seems to be Fedora. Fedora is free. Can one purchase a laptop with Fedora exclusively installed?
Spelunking around the Fedora website leaves one a bit dismayed. The policy there seems the opposite of Steve Jobs, to keep things simple.
There were countless times when we, in the run-up to our purchase of Apple products, got waylaid and maliciously lost at the Wintel sites. Trying to find the offer you just saw on the telly? Good luck. And there were suggestions that the people running the websites of those OEMs were just as confused as the site visitors. See our collision with the proprietors of a Gateway Country as an example.
Do we need all that complexity for only the foundation of an OS? Not likely. Do we need more sophistication than currently available with Gnome and KDE? Yes. Ouch. Do we ever. But importantly: do we need to worry about desktop/laptop OSes anymore?
There's the rub. For more and more communications are web-based. Back some twenty years, when we contemplated the 'step' to a NeXT system, that alternative didn't exist. Today it's obvious it might be the only viable one.
People will need desktop/laptop to build web software, but perhaps those desktop/laptop systems aren't as crucial anymore.
That being said, let us continue our inventory of our current 'NeXT' lineup, titles S-Z. Except we're not going all the way to Z. We'll stop before that. The reason may become clear in a week or two.
S3
The SpamStopper Stopper. Perhaps our first title ever. A reaction to an obscenely gross tool we'd found. A simple but useful idea - but a megabyte on disk?
If memory serves, we had a colleague contribute a script that theoretically could make things even simpler - with a script of a few hundred bytes. And, as per usual, the bloat artist developer got nasty. They always do!
The idea: to use alternative characters (escapes) to obfuscate what spam crawlers look for in web pages.
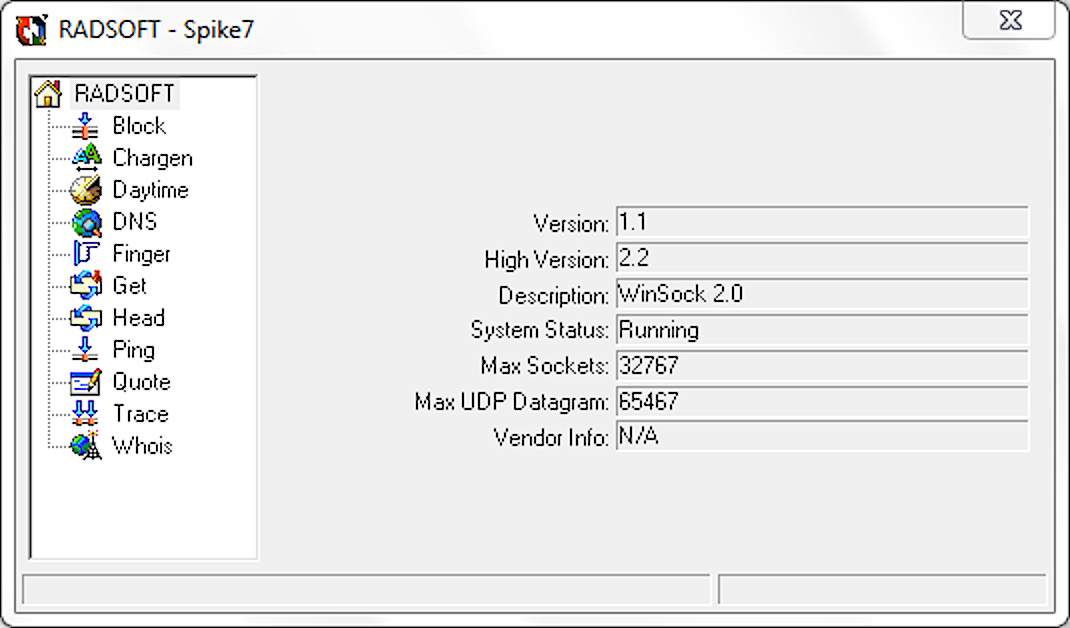
Spike
You've seen Goldeneye? Towards the end of the movie, Izabella Scorupco sends a command to the computer on the train: 'SEND SPIKE'. The name stuck. Spike is a general-purpose network utility that beats the pants off the competition on Windows (and is arguably prettier as well).
The OS X version's OK and has proven very useful. Sad about the demise of GeekTools which was the goto for Whois all these years. But as the people behind GeekTools point out, a simple command-line 'whois' will do nicely today. As for integrating this into Spike: next version, next platform, see you then.
SPX
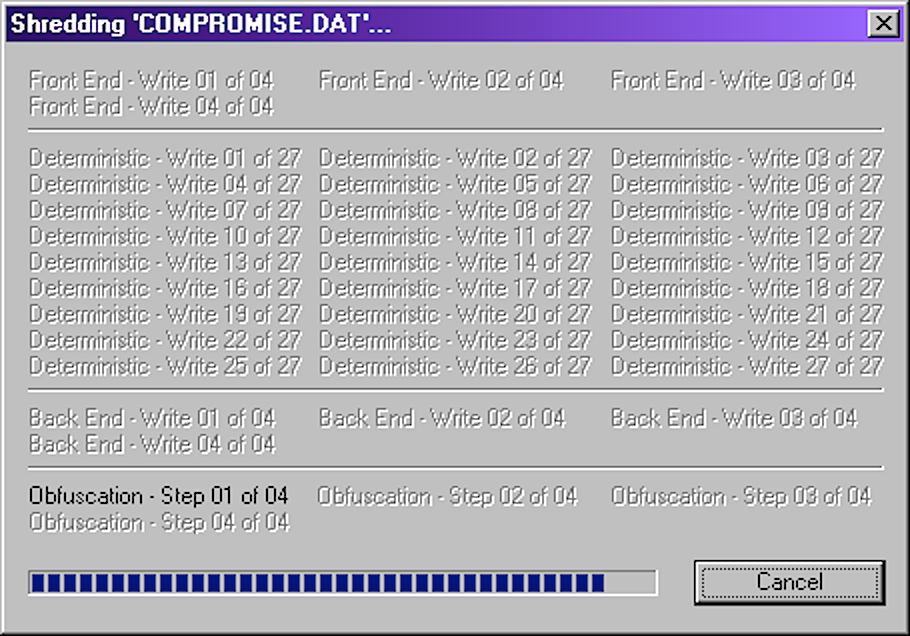
ShredPerfect+ started with an inquiry from Robin Kerr. He needed a shredder and could find none available. So we built one - the first on Windows. It got a writeup in Windows Magazine or whatever it was called. SPX uses Gutmann's 35-step method. Most lame 'programmers' think Gutmann’s ‘35 steps’ are way too difficult. Choose another profession in such case.
Bloat-bomb Eraser's egregious author was in contact with us - not a pleasant person.
Lots of other frills are tossed into SPX, such as shredding the RAM used, shredding the original file name on disk, and so forth.
SPX was, as stated, the first such shredder available on Windows, and the first-ever on Apple's OS X as well.
(A consumer warning here, for using a shitty shredder can be worse than not shredding at all. For shredders normally conclude by removing the target file from the file system, and if the file isn't properly shredded, you're not going to be able to find it, whereas forensic specialists can.)
The SPX engine was incorporated into our E3 Security Kit, which in turn was a direct reaction to one of the Internet's greatest scams of all time, Evidence Eliminator.
Evidence Eliminator (EE) was code bought by one Andy Churchill of Nottingham UK. It's what he did with that code that made the difference - and caused the uproar. It was how he peppered the code with scare screens and then paid commissions to resellers who absolved him of legal repercussions and went on to do all the really despicable stuff - that's what made the difference.
We have an entire section of the Radsoft website devoted to exposing the EE scam. Our Bloatbusters buddies also did a review.
We'd developed a routine of exactly duplicating bloat monsters at a tenth or so of a percent of their disk footprint, just to show how lame programmers could be. (Yes it's that bad. No arcane secrets or secret APIs, you just don't code with your head up your arse.) We did the same for the original E3. It took several weeks. Then just as we'd begun sending out the notifications about the upload, we got a lightbulb and stopped the transmission. Why duplicate bad design for something this important? We got back to work. Another few months and we'd developed an armada of security tools, known thereafter as E3 Security Kit.
The effort paid off. Unknown to us at the time, a sort of skunkworks at the Pentagon had been looking into buying EE, as there didn’t appear to be any alternatives available. Then they found us and our E3. Their point man spent nearly two years lobbying his superiors at the DOD to please not buy EE but buy our E3 instead. We ended up contracting a site licence to the Pentagon.
This 'point man' and I, with me working in my sick bed, toiled for 23 hours (mostly straight through) on his final report to his boss right before Xmas 2003. The report included specific routines for using the system so human error couldn't foul anything up. Most of those 23 hours were spent hacking out those routines.
We settled on a dumb terminal solution, so the OS wasn’t resident on local disk but instead was first loaded from a server on login. This image included startup routines which made sure our E3 was running either right after login or right after logout or both.
The Pentagon point man wrote a lyrical letter of reference as a 'thank you', professing he'd never before seen such devotion to quality. Very nice. And thank you. It was fun! And so glad to be of service.
As a final request, he painted the following scenario. Imagine one of our 150 staffers has to take a laptop to an overnight destination such as a motor lodge or hotel. How safe is that? That laptop may have sensitive information. We'd need to make sure that laptop is secure at nighttime, he said.
Things got a bit tricky. For you didn't want to leave traces on disk of what you'd just done either. So everything had to be kept in RAM and disappeared on application exit.
The laptop user would simply open the laptop at bedtime, leave it open, fire up the application, and go to bed and let it run. Finished by morning.
It worked like a charm. We used a suspension bridge at night as a graphic. The point man was pleased, but then he asked:
'Those lights on the suspension bridge: is there any way you can make them blink?'
'Nooooooooooooooooooooooo!'
The utility is known as E3 Nighttime.
The Pentagon gig led to an even bigger and even more lucrative contract with a major international telco.
As for what they were up to over there: we never asked, they never said. But we asked IBM people we knew. Many had heard of them, many rolled their eyes when they heard the name, some turned a whiter shade of pale, but no one offered any details. Until someone finally said:
'You've heard of the fifty-dollar toilet seats?'
We were eventually able to get further details, but we're not going to say.
SPXN
SPX Nighttime. The OS X equivalent of E3 Nighttime.
Swap
Apple's HFS has an empty CNID slot which is used to swap files in place. Given the demise of HFS, we had to come up with a secure method of doing this the conventional way. This is it. Includes rollback logic 'just in cases'.
Swapwatch
Apple's virtual memory system isn't exactly industry standard (where Dave Cutler's was) so it became necessary to keep an eye on swap usage, so one knew when rebooting was necessary.
Because it often was (and even today with SSH sometimes is).
TempEdit
Part of a Rixstep invention. The trick as always is to enhance existing applications across the board without in any way poking into their code.
TempEdit stands for 'Template Edit’, where 'template' is a character string to be inserted into a text file at caret location. Little Nerd Aaron had something similar on the way, but it was sketchy, NIB menu-based, so not flexible.
TIFFCompress
To this day, and for who knows what reason, the algorithm used in this app compresses your non-lossy TIFF files better than Apple's system utilities. And TIFFCompress only compresses if there's a win.
Savings are listed. Very precise, very fast.
TMI
Too Much Information. No idea how this began. Target audience was Unix newbies. Can of course be ported to other Unix platforms.
Tracker
This one took work. There's nothing like it even today. No one else has this functionality. No one. You'd think the lamers running Apple systems would want something else in competition, but no. They used AppZapper. Goodness gracious, watching them compare similar AppZapper utilities - you cannot believe how thick people can be.
No way to remember how this began. The need was palpable. Going back to Windows/Bloatbusters days. There was a particularly unsavoury Norwegian company. Opera. (Is 'Opera' a good name for a web browser?) They were vicious. Their Nazi fanboys were worse. We had users of Silencer (from the Bloatbusters) who inquired about compatibility with Opera. We'd never used Opera, so we downloaded it to see if compatibility was possible.
The long and short of it was that Opera never worked, and Opera support staff told us we had to wipe and reinstall our entire OS to make it work. We threatened with legal action, which is when, after several days of mucking about, a representative of Opera connected to us through an IP not part of the Opera domain.
It's in WIN.INI, he told us, in an effort to avoid the threat of a lawsuit. They snuck an obscure key in WIN.INI to thwart 'improper use' of their precious browser. Except the code wasn't all that spiffy. Obviously.
If the Opera nightmare can't convince you of the need for Tracker, nothing can.
Neil Rubenking had a Windows utility that tracked Registry changes. We worked with this utility on our E3 Security Kit.
And the Apple fanboys, running AppZapper... Words can't.
UCS
Universal (Coded) Character Set. The subset of Unicode available as HTML escapes. Divided into three categories. This application domain comes from the real Sir Tim, not the faggy one, so this can indeed be ported.
Undercover
To combat Apple. Yes again. All the two-bit tricks Apple can get up to... This app counterbalances a bit. It 'uncovers' files Apple would love to keep hidden from you. And it covers them up again if that's your wish. Some file manager functionality as well.
XaBatch
Very useful for a while. Assumes extended attributes will be a problem, which they are on Apple platforms but not on other more ‘adult’ Unix platforms.
Facilitates adding or removing XAs in batch. Has a command line counterpart for easy admin scripting (of its own scripts) .
Xattr
Essential. The first third-party utility of its kind anywhere in the world.
A tosser from the UK tried to claim some ten years later that he was first - using the most ungodly vainglorious UI layout ever seen. He didn't last long.
Xattrib
Deals with mostly standard Unix attributes. The system and user flags are platform-dependent.
Xbase
We were in a transition back at our teaching factory in Stockholm. Every week, sometimes more often than that, secretaries would make the rounds, meting out small coloured cards with all the new phone number extensions. New colour every time. Clearly this was wasting time and effort. Keeping sales and marketing in mind, I devised a method to centrally store all extension numbers, simultaneously offering a client version that let sales and marketing jot down notes on clients and potential customers.
This was the first real-life Windows application I'd ever written start to finish. Needless to say, it was a personal milestone, ending a period of nearly one year where I'd put myself through the wringer to finally grok and master hard-core Windows programming. The result was this app, and a slew of offers from European consultancy and teaching companies poured in.
The MSDN discs included lots of stuff like Cinemania, and I created the application Rixreel as a result. Then, and only then, after completing this application, do I realise that yes, this one and the earlier phone extension number one have almost everything in common, as noted much earlier, but, most importantly, they can be melded into the same app where only the column headers are different. Thus Xbase. To exaggerate the usefulness of this app over the years is totally impossible. There's nothing 'Apple' about it. It exists on two platforms already. It should be ported to a third.
Until Next Time!
We'll leave it there for now. For reasons which should become clear in a week or two.
Take care, all. Be safe and Be well.
PS
PS. How many programs did Steve Gehrman produce in over 20 years? One?
Like that gay ‘Red Sweater’ dude (who, no joke, called himself ‘Punkass’) who was given the code to his one and only minimum opus, or the Panicky Boys’ 3-4 titles in the same 20+ years?
You guys need a break. From the software industry.
Bring the adults in.